HashiCorp Boundary Enterprise Crack emerges as a robust solution, providing a comprehensive and secure approach to managing remote access across diverse environments. This blog post will delve into the intricacies of Boundary Enterprise, exploring its features, architecture, and benefits for enterprises seeking to bolster their security posture.
Understanding HashiCorp Boundary Enterprise
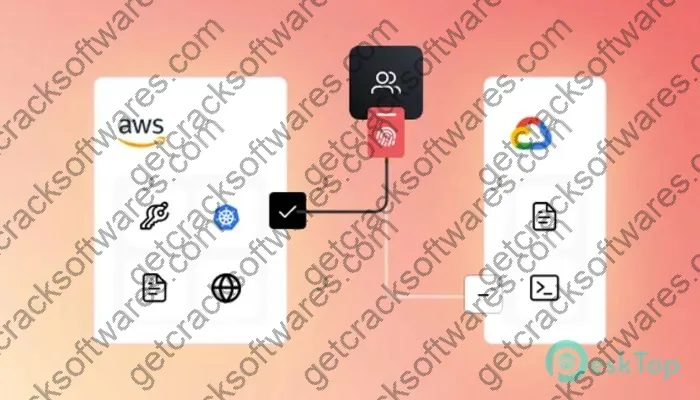
HashiCorp Boundary Enterprise Free download is a unified remote access solution that simplifies and secures access to servers, remote desktops, Kubernetes clusters, and more. It operates on the principle of separating computing resources from the control plane, ensuring that sensitive credentials are never exposed, even to privileged users. This “authorize before authenticate” approach enhances security while streamlining access management.
At its core, Boundary Enterprise employs a robust architecture comprising multiple components:
- Controllers: Act as the centralized control plane, enforcing access policies and managing sessions.
- Workers: Deployed on target systems or environments, facilitating secure connections and executing authorized actions.
- CLIs and Desktop Tools: User-friendly interfaces for interacting with Boundary Enterprise and accessing resources.
The workflow is designed to be seamless yet secure. Users authenticate with Boundary Enterprise, which then authorizes access based on predefined policies. Once authorized, Boundary establishes a secure connection to the target resource without exposing sensitive credentials.
Key Features of HashiCorp Boundary Enterprise
Unified Access for Diverse Resources
Boundary Enterprise provides a centralized platform for managing access to a wide range of resources, including:
- Servers: Securely access and operate servers across on-premises, cloud, and hybrid environments.
- Remote Desktops: Enable secure remote desktop connections for seamless remote work.
- Kubernetes Clusters: Streamline access to Kubernetes clusters and applications while maintaining strict access controls.
- Databases: Manage and secure access to databases without exposing sensitive credentials.
Multi-Cloud and Hybrid-Cloud Support
With its cloud-agnostic architecture, Boundary Enterprise seamlessly integrates with major public cloud providers, such as AWS, Azure, and GCP, as well as on-premises and hybrid deployments. This flexibility ensures consistent access management across diverse infrastructure environments.
Identity-Based Access Controls
Boundary Enterprise Activation Code leverages identity and role-based access controls (RBAC) to manage user permissions and access levels granularly. This approach aligns with the principle of least privilege, minimizing the attack surface and reducing the risk of unauthorized access.
Credential Injection and Management
Sensitive credentials, such as SSH keys or database passwords, are securely injected into authorized sessions without being exposed to users or administrators. This mitigates the risk of credential theft and improves overall security.
Logging, Auditing, and Monitoring Capabilities
Boundary Enterprise provides comprehensive logging, auditing, and monitoring features, enabling organizations to track and review access events, user activities, and system health. This transparency promotes accountability and aids in incident response and compliance efforts.
Enterprise Scalability and High Availability
Designed for enterprise-grade deployments, Boundary Enterprise offers scalability and high availability, ensuring uninterrupted access to critical resources even during peak usage or system failures.
See also:
Enhanced Security with Boundary Enterprise
Boundary Enterprise’s unique security approach sets it apart from traditional remote access solutions:
- Credential Protection: By never exposing sensitive credentials, Boundary Enterprise mitigates the risk of credential theft and misuse.
- Secure Sessions: All remote access sessions are encrypted and secured, preventing unauthorized eavesdropping or tampering.
- Granular Permissioning: Fine-grained access controls ensure users can only access the resources they’re authorized for, minimizing the impact of potential breaches.
- Compliance and Auditing: Comprehensive logging and auditing capabilities aid in meeting regulatory requirements and security best practices.
Boundary Enterprise has undergone rigorous third-party security audits and certifications, further validating its robust security posture.
Setting Up and Using Boundary Enterprise
Deploying Boundary Enterprise Crack involves setting up the necessary components, such as Controllers and Workers, across your infrastructure. The installation process is straightforward and well-documented, with support for various deployment methods, including:
- Manual installation
- Automated deployment with configuration management tools (e.g., Terraform, Ansible)
- Containerized deployments (e.g., Docker, Kubernetes)
Once deployed, administrators can configure resources, roles, and projects through Boundary Enterprise’s intuitive interfaces or APIs. Users can then access authorized resources securely using the Boundary Desktop application or command-line tools.
Boundary Enterprise provides comprehensive monitoring and management capabilities, enabling administrators to track system health, review access logs, and manage user permissions centrally.
Boundary Enterprise vs. Boundary Open Source
While HashiCorp offers a free, open-source version of Boundary, the Enterprise edition provides additional features and capabilities tailored for enterprise-scale deployments:
- SAML and OIDC Integration: Seamlessly integrate with enterprise identity providers for streamlined user authentication and access management.
- Enhanced Auditing and Logging: Gain deeper insights into user activities and access events with advanced auditing and logging features.
- Enterprise Support and SLAs: Access priority support channels, guaranteed response times, and service level agreements (SLAs) for mission-critical deployments.
- Advanced Scalability and High Availability: Benefit from enhanced scalability and high availability features designed for large-scale, mission-critical environments.
The Enterprise edition is recommended for organizations with strict security requirements, regulatory compliance needs, and mission-critical workloads that demand enterprise-grade support and advanced features.
See also:
Integrations and Compatibility
Boundary Enterprise Patch integrates seamlessly with various identity providers, cloud platforms, and infrastructure components, ensuring a consistent and secure access experience across your technology stack. Some notable integrations include:
- Identity Providers: SAML, OIDC, Active Directory, and more
- Public Cloud Platforms: AWS, Azure, GCP
- Container Orchestration: Kubernetes
- Infrastructure as Code: Terraform, Ansible, and other configuration management tools
Additionally, Boundary Enterprise supports a wide range of operating systems, including Linux, Windows, and macOS, ensuring compatibility across diverse environments.
Conclusion
HashiCorp Boundary Enterprise Crack emerges as a powerful solution for organizations seeking to streamline and secure remote access to critical systems and resources. Its robust architecture, advanced security features, and centralized access management capabilities make it an invaluable tool in today’s distributed workforce landscape.
By adopting Boundary Enterprise, organizations can enhance their security posture, simplify access management, and maintain compliance with industry regulations. With its support for diverse resources, multi-cloud environments, and seamless integrations, Boundary Enterprise offers a flexible and scalable solution that can adapt to evolving business needs.
As remote work continues to gain traction, the need for secure remote access solutions will only become more pronounced. HashiCorp Boundary Enterprise positions itself as a future-proof solution, empowering organizations to embrace remote work while maintaining a strong security stance.
The responsiveness is a lot better compared to older versions.
I would strongly recommend this tool to anybody looking for a top-tier platform.
This platform is definitely great.
It’s now far easier to finish jobs and manage information.
I would definitely recommend this application to anybody looking for a robust solution.
The new functionalities in update the latest are extremely cool.
It’s now much more user-friendly to get done tasks and organize content.
I love the enhanced dashboard.
It’s now a lot simpler to get done jobs and organize data.
It’s now much more user-friendly to do projects and track information.
The recent enhancements in release the newest are extremely awesome.
I would definitely recommend this tool to anyone wanting a high-quality product.
It’s now far simpler to get done projects and track data.
I appreciate the improved dashboard.
I would definitely suggest this program to anyone looking for a powerful platform.
The responsiveness is significantly better compared to last year’s release.
I love the new interface.
The recent updates in release the latest are so useful.
The responsiveness is significantly faster compared to the original.
I would definitely suggest this program to anyone wanting a robust platform.
It’s now much more intuitive to do jobs and track content.
The speed is significantly enhanced compared to the original.
I would highly suggest this application to anybody looking for a top-tier product.
I appreciate the new layout.
It’s now far easier to do tasks and manage information.
It’s now far more intuitive to do tasks and track content.
The speed is significantly improved compared to older versions.
I appreciate the improved workflow.
The latest functionalities in update the latest are incredibly awesome.
I appreciate the new interface.
The software is absolutely great.
The new enhancements in update the latest are really helpful.
This tool is absolutely great.
The recent updates in version the newest are so awesome.
I appreciate the upgraded dashboard.
The application is absolutely impressive.
I really like the improved interface.
The software is definitely awesome.
This software is truly great.
This application is absolutely fantastic.
It’s now a lot more intuitive to finish work and organize content.
The platform is absolutely great.
The application is absolutely fantastic.
I love the enhanced interface.
The responsiveness is significantly enhanced compared to the original.
The responsiveness is a lot improved compared to older versions.
The application is really impressive.
The speed is so much faster compared to the previous update.
The new updates in release the latest are extremely cool.
The platform is really amazing.
It’s now much more intuitive to do work and organize data.
It’s now a lot more intuitive to complete projects and track content.
I appreciate the improved UI design.
The recent updates in version the latest are extremely great.
I would definitely endorse this tool to professionals looking for a powerful platform.
I would definitely endorse this software to anyone wanting a robust solution.
I would highly suggest this software to anybody needing a top-tier platform.
The performance is a lot better compared to older versions.
I appreciate the improved interface.
I would absolutely suggest this program to anybody wanting a top-tier product.
I would highly recommend this application to professionals looking for a robust solution.
The speed is significantly enhanced compared to the previous update.
I love the new dashboard.
I absolutely enjoy the improved interface.
It’s now far more user-friendly to finish projects and manage data.
I would strongly recommend this application to anybody wanting a robust product.
The latest updates in release the newest are extremely awesome.
It’s now much easier to do tasks and organize content.
The recent functionalities in version the latest are really helpful.
I appreciate the improved dashboard.
The recent enhancements in version the newest are so awesome.
The responsiveness is a lot better compared to older versions.
I would definitely suggest this software to professionals needing a top-tier solution.
It’s now a lot more user-friendly to complete work and manage information.
It’s now a lot more user-friendly to finish projects and organize information.
I would highly recommend this program to anybody looking for a robust product.
I would absolutely recommend this software to anyone wanting a high-quality solution.
I absolutely enjoy the upgraded interface.
This platform is really impressive.
I love the new dashboard.
The new features in version the latest are incredibly cool.
This program is absolutely impressive.
The recent capabilities in version the newest are really great.
I appreciate the new UI design.
I really like the improved workflow.
I really like the upgraded UI design.
It’s now far easier to finish jobs and track information.
The performance is so much improved compared to last year’s release.
I love the upgraded workflow.
I would definitely endorse this tool to professionals wanting a top-tier product.
It’s now much more user-friendly to complete jobs and organize data.
The recent enhancements in release the newest are incredibly helpful.
I would definitely suggest this software to anyone wanting a robust platform.
It’s now much more intuitive to finish jobs and track content.
The responsiveness is so much improved compared to older versions.
The performance is so much enhanced compared to the previous update.